Hi,
today the update for my Sony XZ2 (Akari) to version 4.1 was offered. Update worked so far. Since my device is rooted via Magisk, I looked in the Github repo for a recovery zip for 4.1, but there was only recovery 4.0. So I changed to fastboot and put the old patched recovery from version 4.0 to the phone, but the reboot got stuck at the Sony logo. Then I loaded the original 4.0 recovery via fastboot to the phone, again stuck at the Sony logo:-(
In the repo is a new archive iode-4.1-20230401-akari-fastboot.zip size of 1,3 GB
I tried to install this archive via adb, but that failed with error 21 signature verification failed.
Finally I installed iode-4.1-20230401-akari.zip via adb and the system runs again, but I don’t know how to reactivate Magisk again, since there is no 4.1 recovery.
So my questions: where is 4.1 recovery for akari
what is the file iode-4.1-20230401-akari-fastboot.zip for?
Regards
We have not updated the installation instructions yet, this will be done today. The fastboot package contains a script that fully installs the rom, without having to switch between fastboot/recovery… it’s far easier. The recovery can be extracted from the fastboot package, in the img zip (boot.img, as it is kernel+recovery for xz2).
I’ve not yet managed to extract a recovery.img from the iode-4.1-20230401-akari-fastboot.zip, neither with 7z, WinRAR nor with the jack-of-all-trades PowerArchiver.
BTW: Extracting the payload.bin does not bring up recovery.img either.
Well, I helped myself OrangeFox Recovery, but I can’t see that it has become much easier, as mentioned!
Why is there now a difference in ROM file creation between devices?
There is no payload.bin in iode-4.1-20230401-akari-fastboot.zip ; however, there is one in iode-4.1-20230401-akari.zip : I think you looked in the wrong file.
And: there is no recovery.img, but boot.img, that must be flashed to the boot partition. It contains the kernel and the recovery.
The fastboot flashing method is much easier: you uncompress a zip file, you just need to have fastboot (adb not required), you execute a script, and eveything is done. No need to flash the recovery , to enter it, to sideload… Only samsung devices do not support this method, all other devices do.
No. I’ve extracted both files: iode-4.1-20230401-akari-fastboot.zip + iode-4.1-20230401-akari.zip
As I previously said:
And thus:
$ unzip iode-4.1-20230401-akari-fastboot.zip
Archive: iode-4.1-20230401-akari-fastboot.zip
creating: iode-4.1-20230401-akari-fastboot/
extracting: iode-4.1-20230401-akari-fastboot/iode-4.1-20230401-akari-img.zip
inflating: iode-4.1-20230401-akari-fastboot/flash-all.bat
inflating: iode-4.1-20230401-akari-fastboot/flash-all.sh
$ unzip -l iode-4.1-20230401-akari-fastboot/iode-4.1-20230401-akari-img.zip
Archive: iode-4.1-20230401-akari-fastboot/iode-4.1-20230401-akari-img.zip
Length Date Time Name
--------- ---------- ----- ----
24 2008-01-01 00:00 android-info.txt
67108864 2008-01-01 00:00 boot.img
8388608 2008-01-01 00:00 dtbo.img
2213999376 2008-01-01 00:00 system.img
250316 2008-01-01 00:00 userdata.img
8192 2008-01-01 00:00 vbmeta.img
699560240 2008-01-01 00:00 vendor.img
--------- -------
2989315620 7 files
And so on - that’s exactly the point. Yes, I also got as far as you indicated. But when I extract the boot.img, no recovery.img is revealed. Please tell us the trick, @vince31fr
I already explained twice.
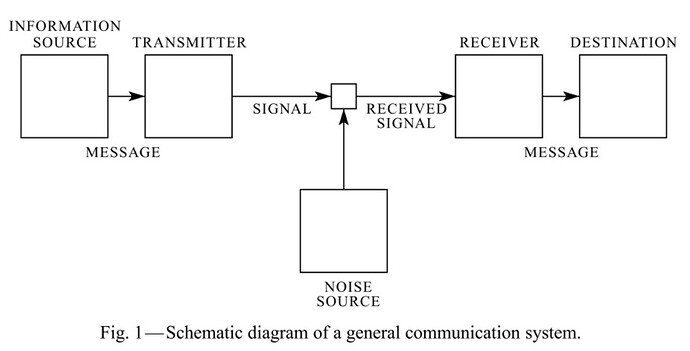
When people communicate with each other, they become senders and receivers. The sender wants to communicate something, for example views or factual information. However, this is not done by thought transmission, but what is to be expressed is encoded. Speech or writing “transports” the message to the receiver. In other words, a signal is sent out.
The receiver has to decode the signal again. Only when he has “cracked” the code and interpreted the message can he react to it and become a sender himself.
Sender-receiver model (according to W. Weaver/C. E. Shannon: The Mathematical Theory of Communication, Illinois 1949)
Use the boot.img file as recovery, I patched that file with Magisk and now I have root access again with 4.1